Jobsity’s Security Tip Number Three: Zero Trust Network

We have discussed two main security tips in our previous blog post concerning VPNs and Passwords. The last tip we would like to dive into is regarding the Zero Trust Network. This is the newest way of thinking in cyber security, especially for remote teams. For us, it is important to provide you with all of the tools that can help manage your team in the most secure and convenient way.
Let's start with explaining what Zero Trust Network is (it is also known as Zero Trust Architecture). It is a set of paradigms that ensure no user, no access, and no digital identity is granted access to a system or network based on simple unquestioned identifiers like network ID or physical location. In a simpler way, according to CSO, Zero Trust Network “is a security concept centered on the belief that organizations should not automatically trust anything inside or outside its perimeters and instead must verify anything and everything trying to connect to its systems before granting access.”
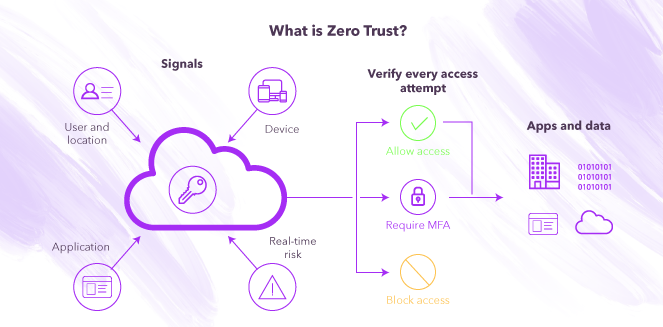
Zero Trust does not depend on a location, we have to take into consideration that users, apps, and devices are everywhere nowadays. Zero Trust must be replicated through your whole environment to make sure that each person of your team has access to the corresponding data.
Something to be really clear about Zero Trust is that it tends to assume breaches. It verifies every request as if they all originate from an open network, therefore, it teaches us to “never trust, always verify.”
Moving forward, it is important to understand Zero Trust’s principles and how it functions;
- First, it is important to assume that attacks can be made within or outside the network, so no user or machine should be trusted automatically.
- Second, give users access to only what is necessary depending on their role or position inside the company. This minimizes the risk of exposing confidential information. This is also called micro-segmentation, that is the practice of separating the network and giving access to certain parts to each person inside the team.
- Third, use MFA (we discussed this in the last blog post) to make sure users pass through different types of identity verifications to make sure the correct person or machine is entering the network. It is best to have control on the devices used within the network and for IT to acknowledge and provide access to the selected devices. It is imperative to make sure if the devices are authorized or not. With Zero Trust, all users and all devices will need to pass authentication as discrete functions (2-step verification, FaceID, etc) before any and every enterprise resource session is established. It is, simply put, a way of thinking about security in absolute terms: no one enters anything until they are verified. Such thinking ensures that security is the priority, over ease of use, speed, or functionality of access.
- Fourth, risk-adaptive security controls identify human risky activities in near real-time and take control, this is also known as Continuous Adaptive Risk and Trust Assessment (CARTA).
To implement this type of security there are some guidelines to take into consideration: (vendors provide this type of guidance if your company doesn't have a strong IT team)
- Find a tool that will give network protection, decrypts traffic and guides you with micro-segmentation. In other words, find a next generation firewall.
- Find risk-adaptive security tools so it is easier to apply adaptive controls over your network.
- Activate MFA, you can choose different steps to complete and even find the appropriate vendor that is more suitable for your company.
- Reference your team, it is necessary to understand individuals needs for access depending on their role within the organization. Take caution and remember to give the least amount of access possible.
- Educate your team and create a company culture based on security so the adaptation to the process is easier.
To conclude, this new architecture will help your organization work in a more secure way and protect your information from breaches. We recommend that you implement everything we have discussed in our blog post series. Keep connected to our blog posts, we will continue to post relevant information to help you manage your remote team and adapt to this new normality.
--
If you want to stay up to date with all the new content we publish on our blog, share your email and hit the subscribe button.
Also, feel free to browse through the other sections of the blog where you can find many other amazing articles on: Programming, IT, Outsourcing, and even Management.

Santiago Mino, VP of Strategy at Jobsity, has been working in Business Development for several years now helping companies and institutions achieve their goals. He holds a degree in Industrial Design, with an extensive and diverse background. Now he spearheads the sales department for Jobsity in the Greater Denver Area.